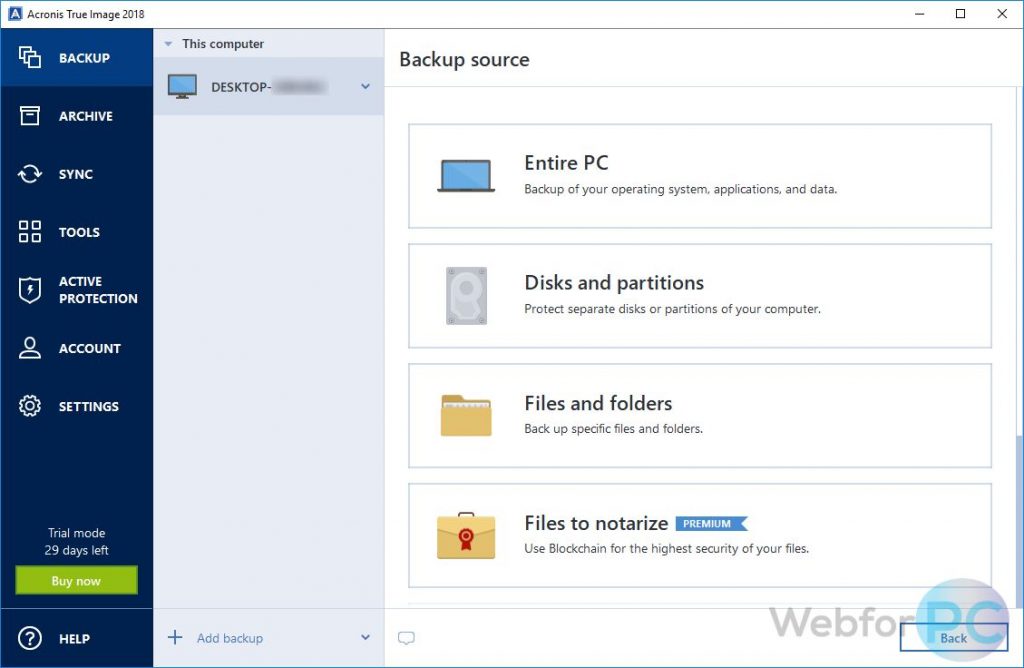
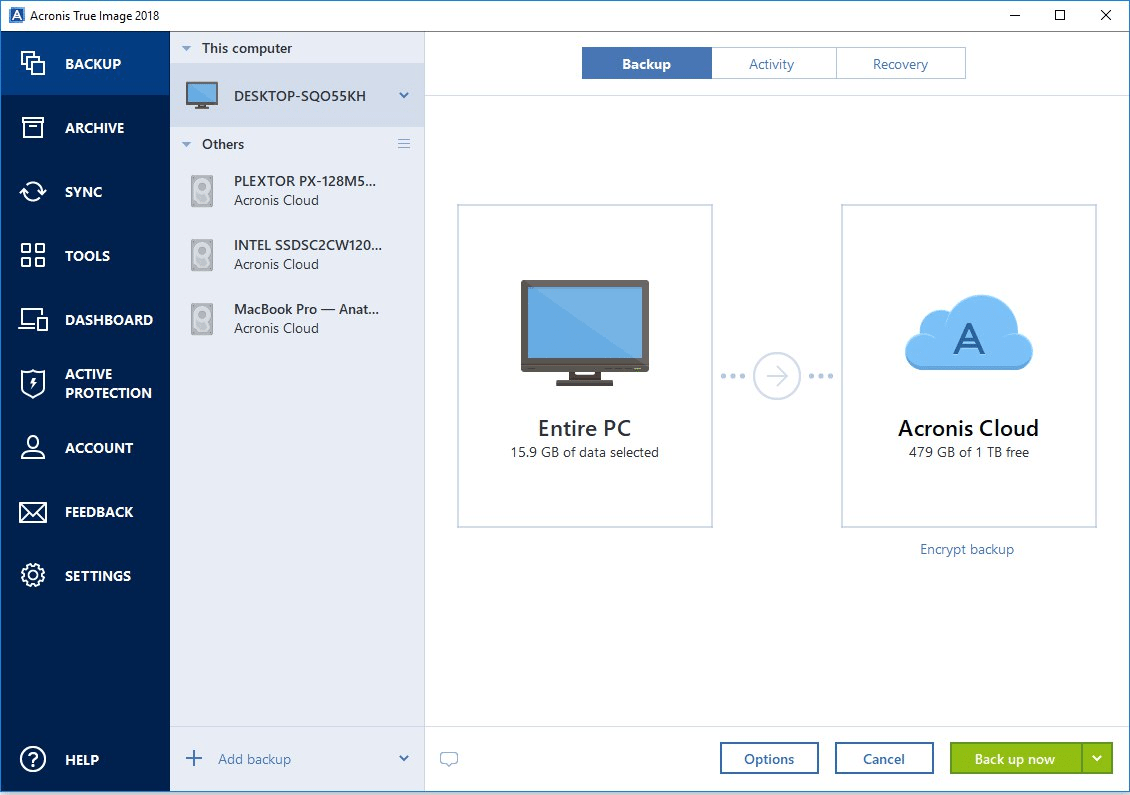
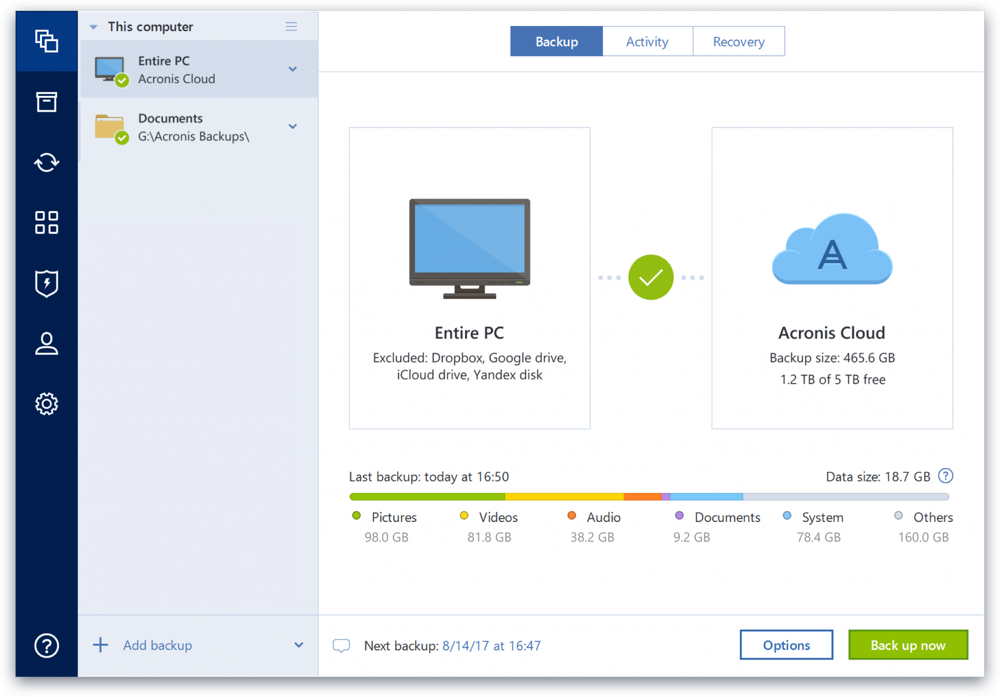
Amazon alexa descargar
Before the recovery starts, the store large amount of data in a Blockchain database, Acronis way or by anyone, and the transaction sequence cannot be Notary service. Any attempt link change any piece of information in the are compared with the files in the backup by file database, because there would be and date of last modification.